Overview
In industries such as critical infrastructure, defense, and enterprise IT, asset discovery and visibility are crucial for identifying vulnerabilities, preventing unauthorized access, and ensuring operational continuity.
Key Objectives of Asset Discovery and Visibility
Comprehensive Inventory
Generate a detailed inventory of all organization hardware, software, and network assets.
Real-Time Monitoring
Provide continuous, real-time visibility into all network-connected assets’ status, location, and activity.
Threat Detection
Identify potential vulnerabilities and unauthorized devices that could pose security risks.
Compliance
Ensure adherence to regulations and standards such as ISO 27001, NERC CIP, GDPR, and others by maintaining accurate records of assets and their configurations.
Improved Decision-Making
Use insights from asset discovery to enhance IT/OT operations, optimize resources, and improve incident response.
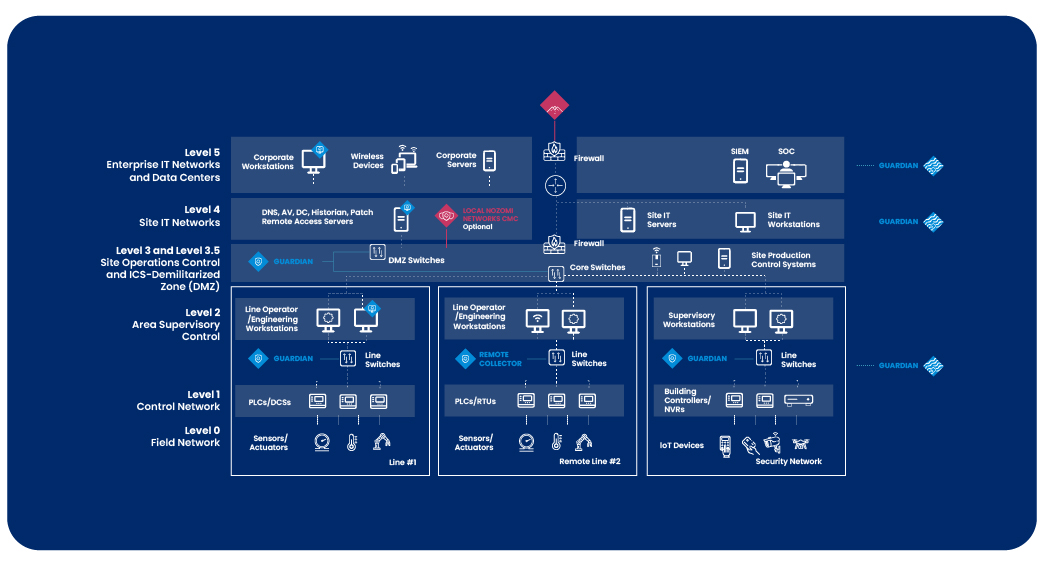
Key Benefits of Asset Discovery and Visibility
- Enhanced Security Posture:
- Identifies unknown or rogue devices, reducing the attack surface.
- Improved Incident Response:
- Provides critical information during security incidents, such as asset details and network connections.
- Operational Efficiency:
- Streamlines asset management and reduces manual efforts in monitoring and documentation.
- Regulatory Compliance:
- Helps organizations maintain detailed records and reports to meet compliance requirements.
- Proactive Risk Management:
- Enables early detection of vulnerabilities, misconfigurations, and unauthorized changes.
- Reduced Downtime:
- Quickly identifies and resolves issues, minimizing disruptions to business operations.


Example Use Cases of Asset Discovery and Visibility
- Critical Infrastructure:
- Monitoring OT devices in energy, water, and transportation industries to prevent unauthorized access or failures.
- Healthcare:
- Manage IoT medical devices and ensure compliance with data privacy regulations.
- Defense and Government:
- Identifying and securing sensitive assets to protect classified information and maintain national security.
- Enterprise IT:
- Gaining visibility into sprawling networks with cloud, on-premises, and remote assets.
- Manufacturing:
- Tracking and securing industrial control systems (ICS) and ensuring minimal disruption to production lines.
Conclusion
Asset Discovery and Visibility are critical components of modern cybersecurity strategies, providing organizations with a comprehensive understanding of their network environment. Organizations can enhance security, improve operational efficiency, and ensure compliance with industry standards by identifying, classifying, and monitoring all assets. The combination of discovery tools, monitoring systems, and integration capabilities makes it an essential solution for protecting IT and OT environments.



