Overview
Browser isolation is a cybersecurity solution designed to shield users and organizations from web-based threats by running browsing activities in a secure, remote environment. Rather than interacting directly with potentially harmful web content, the user's browser session is executed within a containerized or virtualized environment, preventing threats from affecting local devices and networks.
This technology is crucial for mitigating risks such as malware, phishing, drive-by downloads, and zero-day vulnerabilities. It is commonly used in industries like finance, government, defense, and critical infrastructure to safeguard sensitive systems and data from web-based attacks.
This technology is crucial for mitigating risks such as malware, phishing, drive-by downloads, and zero-day vulnerabilities. It is commonly used in industries like finance, government, defense, and critical infrastructure to safeguard sensitive systems and data from web-based attacks.
Key Objectives of IoT Security
Threat Prevention
Block malware, ransomware, and phishing attacks before they reach the user’s device.
Data Protection
Prevent unauthorized data exfiltration by isolating risky websites or links.
Secure Web Access
Provide users with safe browsing capabilities without compromising functionality or user experience.
Zero-Day Protection
Neutralize new and unknown threats that traditional security tools may miss.
Regulatory Compliance
Ensure secure web usage aligns with GDPR, ISO 27001, and PCI DSS standards.
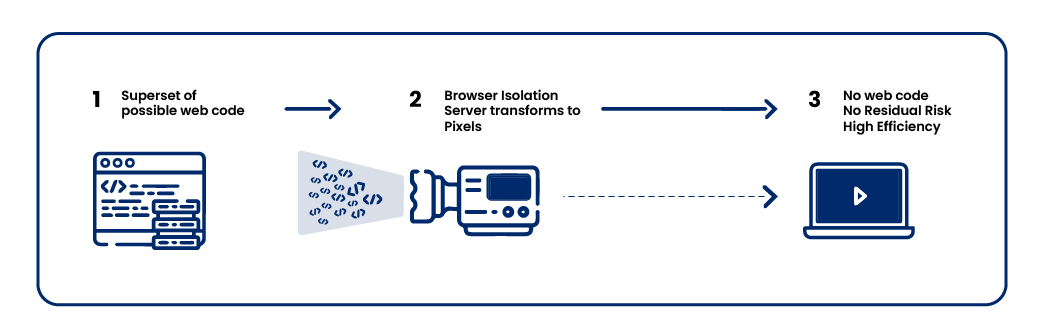
Key Benefits of Browser Isolation
- Enhanced Security:
- Prevents threats from reaching the endpoint, reducing the risk of malware infections and phishing attacks.
- Zero-Day Protection:
- Isolates untrusted or unknown websites, providing proactive defense against emerging threats.
- Data Loss Prevention (DLP):
- Blocks unauthorized file uploads, downloads, and data exfiltration attempts.
- Seamless User Experience:
- Allows users to browse the web safely without noticeable delays or interruptions.
- Regulatory Compliance:
- Helps organizations adhere to data security and privacy regulations by ensuring secure web usage.
- Reduced Attack Surface:
- Keeps all web-based threats in a remote environment, preventing lateral movement in the network.


Use Cases of Browser Isolation
- Government and Defense:
- Protects classified systems by isolating user web activities and preventing exposure to malicious content.
- Financial Institutions:
- Secures online banking and transaction portals from phishing and malware threats.
- Healthcare:
- Safeguards access to sensitive patient data while enabling secure browsing for research or operational needs.
- Critical Infrastructure:
- Ensures secure web interactions for OT and ICS networks without exposing critical systems to web-based risks.
- Enterprise IT:
- Provides secure web access for employees, contractors, and partners, reducing risks from untrusted websites.
Types of Browser Isolation
- Remote Browser Isolation (RBI):
- Browsing activities are processed on a remote server; only sanitized outputs are sent to the user.
- Best for: Highly secure environments and zero-trust architectures.
- Local Browser Isolation:
- Browsing activities are in a secure, isolated container on the user’s device.
- Best for: Lightweight deployments with minimal network latency.
- Cloud-Based Browser Isolation:
- Sessions are processed in the cloud, offering scalability and ease of deployment.
- Best for: Organizations with distributed teams and dynamic workloads.

Conclusion
Browser isolation is a powerful security solution that protects organizations from emerging web-based threats. By isolating browsing activities in secure environments, it allows users to safely access the web without risking the integrity of sensitive systems or data. With capabilities such as threat neutralization, real-time monitoring, and seamless integration, browser isolation has become a key component of cybersecurity strategies across a wide range of industries.



