Overview
CDR is widely used in industries such as government, defense, critical infrastructure, and enterprise IT, where secure file transfer and handling are essential.
Key Objectives of Content Disarm & Reconstruction (CDR)
Threat Neutralization
Proactively removes malicious code, scripts, or macros embedded within files to prevent potential cyberattacks.
File Integrity Preservation
Ensures the sanitized files remain functional and retain their original format and usability.
Prevention of Zero-Day Attacks
Eliminates threats without relying on signature databases or known malware indicators, making it effective against zero-day vulnerabilities.
Compliance
Assists organizations in meeting security standards such as ISO 27001, GDPR, and NIST by safeguarding sensitive data exchanges.
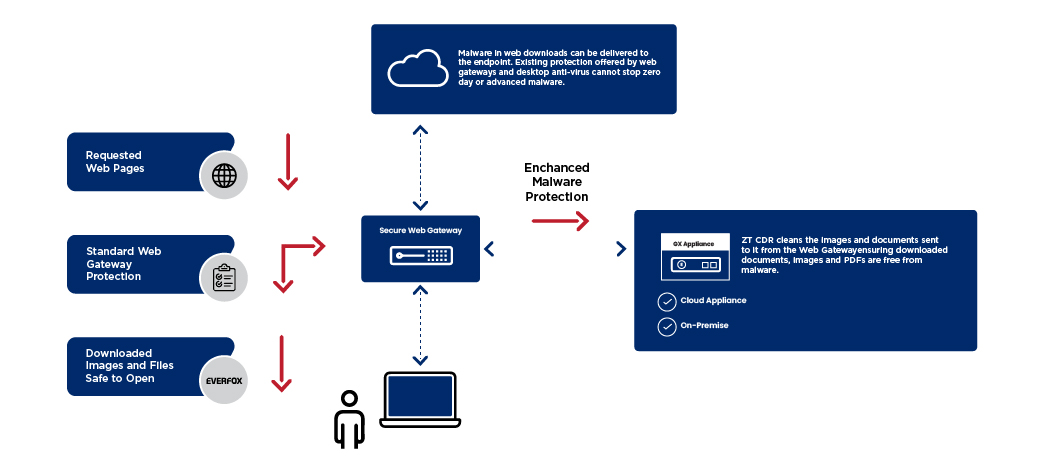
Workflow
- File Ingestion: Files are received from external or internal sources (e.g., email attachments, uploads, or file transfers).
- File Decomposition: The file is broken into core elements (e.g., metadata, content, scripts).
- Threat Removal:Malicious elements are stripped from the file. Examples include:
- Macro removal from Word documents.
- JavaScript removal from PDFs.
- Embedded executable code removal.
- File Reconstruction: A clean version of the file is rebuilt, retaining its original format and usability.
- Delivery: The sanitized file is sent to the intended recipient or destination, ensuring it is safe to access.
- Monitoring and Auditing: All file processing activities are logged for monitoring and compliance.

Key Benefits of Content Disarm & Reconstruction (CDR)
- Proactive Threat Protection:
- Eliminates threats before they can execute, providing an additional layer of security.
- Zero-Day Defense:
- Neutralizes threats without relying on known malware signatures or behavior patterns.
- Maintained Usability:
- Reconstructed files retain their functionality, ensuring that productivity is not impacted.
- Regulatory Compliance:
- Meets stringent security and privacy requirements for handling sensitive data.
- Enhanced Operational Efficiency:
- Automates file sanitization, reducing the burden on security teams.
Use Cases of Content Disarm & Reconstruction (CDR)
- Government and Defense:
- Prevents the infiltration of classified networks by sanitizing files received from external sources.
- Critical Infrastructure:
- Protects Operational Technology (OT) environments from file-based malware attacks.
- Healthcare:
- Secures patient records and medical imaging files against embedded threats.
- Enterprise IT:
- Ensures the safety of files exchanged through email, cloud storage, and collaboration tools.
- Financial Sector:
- Protects sensitive financial data during inter-departmental or client communications.

Conclusion
Content Disarm & Reconstruction (CDR) provides an essential layer of security for organizations that handle sensitive files and data. By proactively removing embedded threats and rebuilding safe, usable versions of files, CDR eliminates risks associated with file-based attacks, including zero-day vulnerabilities. With its ability to integrate into existing security ecosystems and maintain compliance with stringent regulations, CDR is an indispensable tool for safeguarding critical assets across various industries.



