Overview
This technology is crucial for sectors such as defense, critical infrastructure, and large enterprises, where secure connectivity is needed for employees, contractors, and third parties accessing sensitive systems. Modern solutions integrate Web Isolation with OT-Specific Secure Access to safeguard both IT and OT environments from evolving threats.
Key Objectives of Secure Remote Access
Isolated Access
Ensures users can interact with resources without exposing the organization to threats like browser-based attacks or untrusted environments.
Data Protection
Prevents unauthorized data transfer or leakage during remote sessions.
Threat Mitigation
Blocks cyber threats, including malware, ransomware, and phishing attempts
Granular Control
Provides role-based access to ensure users only access the authorized resources
Regulatory Compliance
Meets security standards and regulatory requirements for remote access in critical industries
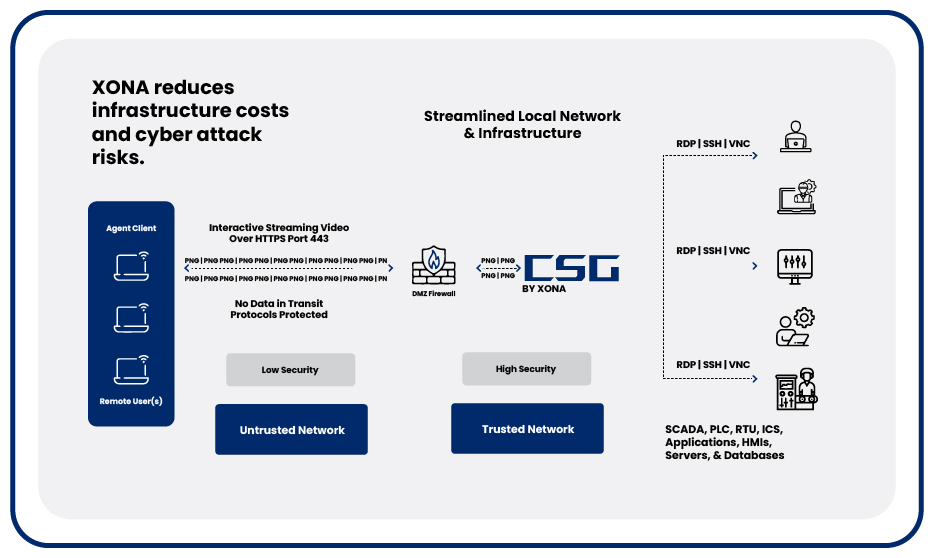
Components of Secure Remote Access Solutions
1. Web Isolation (Browser Isolation)
- Purpose:
- Creates a secure browsing environment by isolating user activities in a remote container to prevent browser-based attacks.
- Features:
- Remote Browser Isolation (RBI): Executes web browsing sessions in a secure environment, delivering only sanitized output to the user.
- Malware Prevention: Blocks malicious scripts, file downloads, and phishing links.
- Content Rendering: Uses pixel streaming or other technologies to ensure users experience a seamless interaction while the actual content is processed in isolation.
2. OT Secure Remote Access
- Purpose:
- Provides secure connectivity to operational technology (OT) networks, ensuring the safety and integrity of critical systems.
- Features:
- Access Control: Role-based access ensures that only authorized users can connect to OT devices.
- Protocol Isolation: Prevents cross-protocol contamination by isolating OT traffic from IT networks.
- Monitoring and Logging: Tracks all user activity to ensure compliance and detect anomalies.
3. Multi-Factor Authentication (MFA):
-
- Ensures only verified users can access sensitive resources by requiring multiple forms of authentication.
4. Secure Gateways:
-
- Acts as an intermediary between users and internal systems, encrypting all traffic and preventing direct access to sensitive resources.


Key Benefits of Secure Remote Access
- Enhanced Security: Protects sensitive resources from unauthorized access, malware, and phishing.
- Operational Continuity:Enables safe access to critical systems, even in remote or emergency scenarios.
- Data Integrity:Prevents data leakage by isolating sessions and enforcing strict access controls.
- Compliance Assurance:Ensures adherence to regulations like GDPR, ISO 27001, and NERC CIP through secure access and audit logging.
- Seamless User Experience:Provides fast and responsive remote access without compromising security.
- Reduced Attack Surface:Isolates threats at the source, ensuring malicious activity does not impact sensitive systems.
Use Cases of Secure Remote Access
- Critical Infrastructure: Securely connects engineers and technicians to OT systems for maintenance and monitoring.
- Government and Defense: Protects access to classified resources by isolating all sessions and monitoring user activity.
- Healthcare: Enables doctors and administrative staff to access patient records securely from remote locations.
- Manufacturing: Allows vendors and third-party contractors to troubleshoot industrial systems without compromising security.
- Enterprise IT: Provides secure access to cloud-based and on-premise resources for remote employees.

Conclusion
Secure Remote Access solutions are indispensable for organizations that balance productivity and security in a remote working environment. Integrating Web Isolation and OT-specific access provides a holistic approach to protecting IT and OT systems from evolving threats. With features like session isolation, real-time monitoring, and multi-factor authentication, organizations can confidently enable remote connectivity while safeguarding critical assets.



